Security breaches that include mobile devices are on the rise with the exponential growth of smartphones. Fraudsters will target any mobile device with more people using smartphones. Each operating system, app, network, and mobile device exploits gaps fraudsters continually find new ways to commit. The more necessary mobile devices become to everyday living and business operations, the more fraudsters will target them.
The Indian government has become proactive about saving the people from the ever-evolving cyber threat landscape. Recently, a warning was issued by The Indian Computer Emergency Response Team, CERT-In, against the possible misuse of public charging ports in cafes, hotels, and airports. These compromised ports pose a massive risk wherein fraudsters will use USB ports to compromise users’ devices when charging.
The government of India is hence taking proactive steps to safeguard the citizens against the ever-changing cyber threat scenario.
What are the risks?
- Data Theft
- Account Compromise
- Device Hijacking
- Credential Theft
- Privacy Violation
Criminals use the USB connection to get to the device’s files, photos, emails, and other private data that is saved on it.
Malware Installation: The fraudster installs malware onto the connected device through the USB connection and steals data, tracks user activities, or compromises security on the mobile device.
Account Compromise: Gaining unauthorised access to the user’s various accounts social media to e-mail, banking, and other online services could lead to identity theft, financial fraud, and other cybercrimes.
Device Hijacking: It remotely hijacks the connected device and leads to several malicious activities, such as sending spam, distributing malware, and attacking other devices or networks.
Credential Theft: The evil charging station or cable can sniff out user credentials like usernames, passwords, and authentication tokens that are either entered or stored on the device.
Privacy Violation: Juice jacking attacks violate users’ privacy, exposing their sensitive and personal information to unauthorised access and use.
Modus of Operandi used by fraudsters to conduct juice jacking fraud
- The impact of juice jacking may vary, but the principle is the same.
- The attackers employ fully automated crawlers to randomly select some easy-to-exploit mobile devices for which PII is available.
- In malware injection, the fraudsters use US budging to load malware onto the connected devices for further spyware or Trojan attacks.
- Threat actors utilise an infected device in a multi-device attack to disseminate malware to other devices. It will likely connect to a USB charging port in the future.
- In a disabling attack, fraudsters lock smartphones through juice jacking so that users may not be able to use their smartphones anymore.
How can Quixxi improve mobile app security and minimise the chance of juice-jacking fraud?
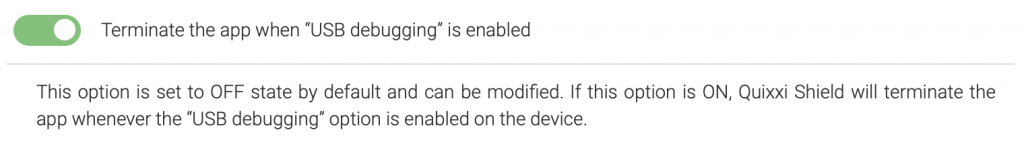
In Quixxi, we provide a shield feature called “USB Debugging,” among others, to detect and prevent any further actions if USB debugging is enabled in the device.
In terms of the “Juice Jacking” issue, enabling the above feature will prevent the user from keeping it on the “USB debugging”, which further prevents injecting malware once it’s connected to the device.
With Quixxi, you can easily improve the security of your mobile apps!
About Quixxi
Quixxi is proud to be the only provider of a patented and proprietary mobile app security solution. Our diversified range of security offerings includes Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Runtime Application Self-Protection (RASP), and continuous threat monitoring.
Quixxi offers mobile app security solutions using AI-based scanners to identify potential vulnerabilities in mobile apps. Their primary service offerings include SCAN, SHIELD, and SUPERVISE. SCAN is a vulnerability assessment tool, SHIELD provides security controls and SUPERVISE monitors runtime applications. Quixxi’s SAAS-based portal targets large enterprise and government organisations with vulnerable applications, focusing on BFSI, Healthcare, and IT service provider industries. They offer one-time and monthly consumer plans and yearly enterprise plans. Quixxi is recognised as a cybersecurity industry leader with numerous awards for its innovative solutions.






