The Android version of the Medusa banking malware has returned after nearly a year-long period of rather low-key activities in France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey.
This new activity has been tracked since May, and it leverages more compact variants that request fewer permissions and bring additional functionalities to perform transactions directly from the infected device. Medusa banking trojan, called TangleBot, is a push-and-file Android malware-as-a-service (MaaS) operation. It was discovered in 2020, which allows for keylogging, screen control, and SMS manipulation-related spyware.
Although it bears the same name, the operation differs from the ransomware gang and the Mirai-based botnet for DDoS operations.
The Cleafy threat intelligence team identified the latest campaigns, which must report that lightweight malware variants require fewer permissions to devices and have added full-screen overlaying and screenshot taking.
Latest Campaigns
The very first evidence of new Medusa variants dates to July 2023, according to experts. Cleafy traced them in campaigns using SMS scams (also referred to as “smishing”) to download malware onto computers via dropper apps. The researchers detected 24 campaigns using the virus and traced them back to five different botnets: UNKN, AFETZEDE, ANAKONDA, PEMBE, and TONY, used to spread malicious programs. The UNKN botnet is run by another different team of threat actors, whose prime target geography includes European countries like France, Italy, Spain, and the UK.
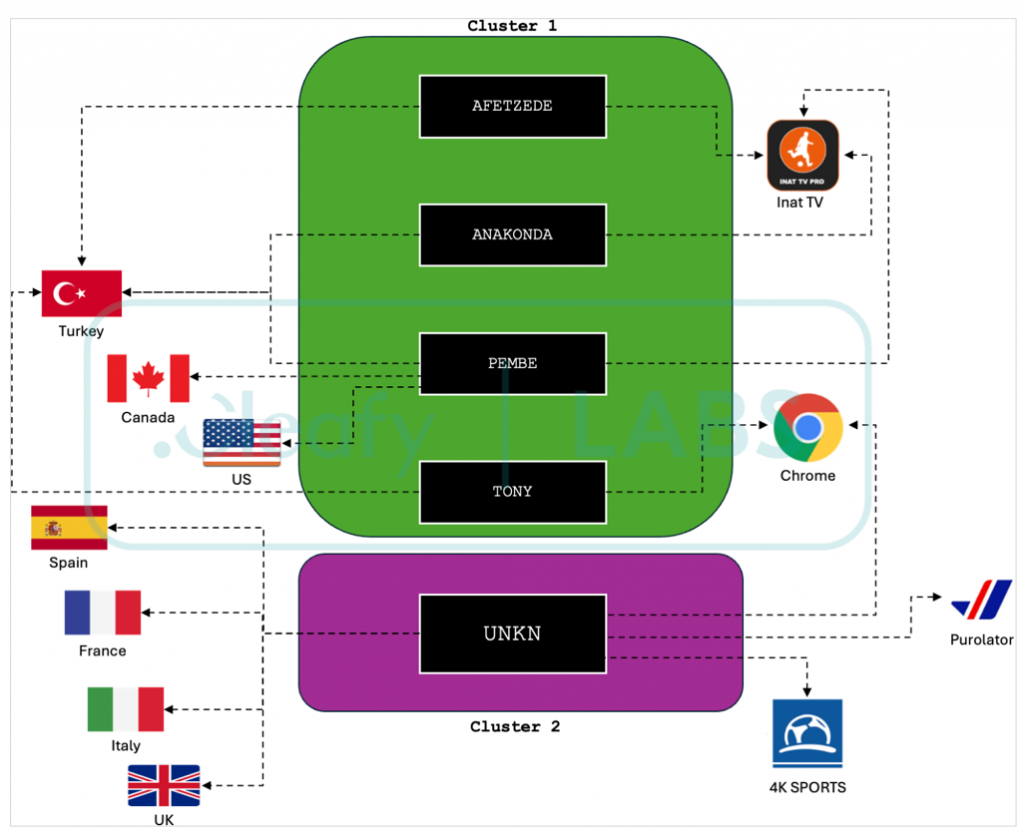
Overview of Medusa botnets and clusters
Source: Cleafy
Some of the recent droppers used in such attacks have been a fake Chrome browser, a 5G connectivity software, and a streaming app malware named 4K Sports. Since the UEFA EURO 2024 championship was ongoing at the time, the exploitation of the 4K Sports streaming software as a lure further creates convenience.
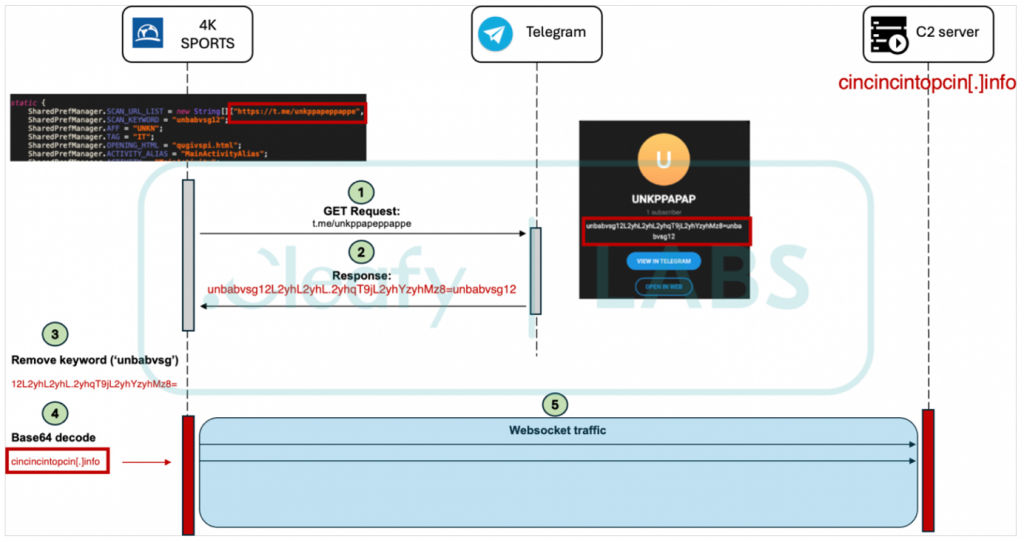
According to researchers, Medusa’s core infrastructure manages campaigns and botnets, and it gets URLs for the C2 server from public social media profiles dynamically.
Retrieving C2 addresses from covert channels
Source: Cleafy
New Version of Medusa
The developers behind the Medusa virus have agreed to reduce its fingerprint on target devices by asking for only a minimal number of permissions but still maintaining the use of Android’s Accessibility Services.
Secondly, this malware can read the content of the target victim’s contact list and even send out SMS, which will, in turn, propagate it.
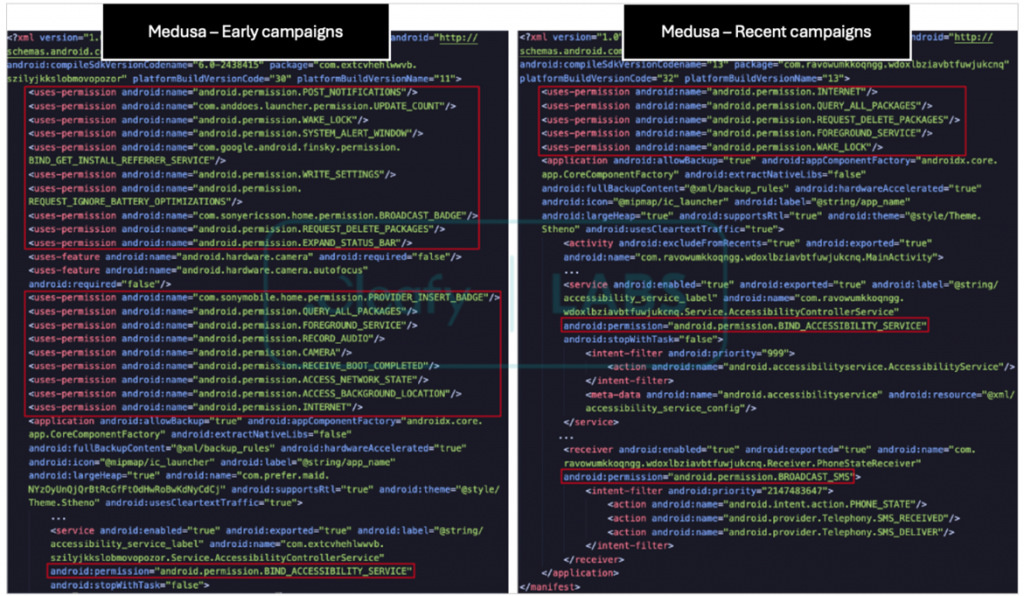
Comparison of requested permissions
Source: Cleafy
The research, according to Cleafy, indicated that the malware authors removed 17 commands from the older variant of infection and introduced five new ones.
These added were:
destroyo: uninstall a certain application.
permdrawover: request “drawing over” permission.
setoverlay: create black screen overlay,
take_scr: take a screenshot
update_sec: update the secret of the user
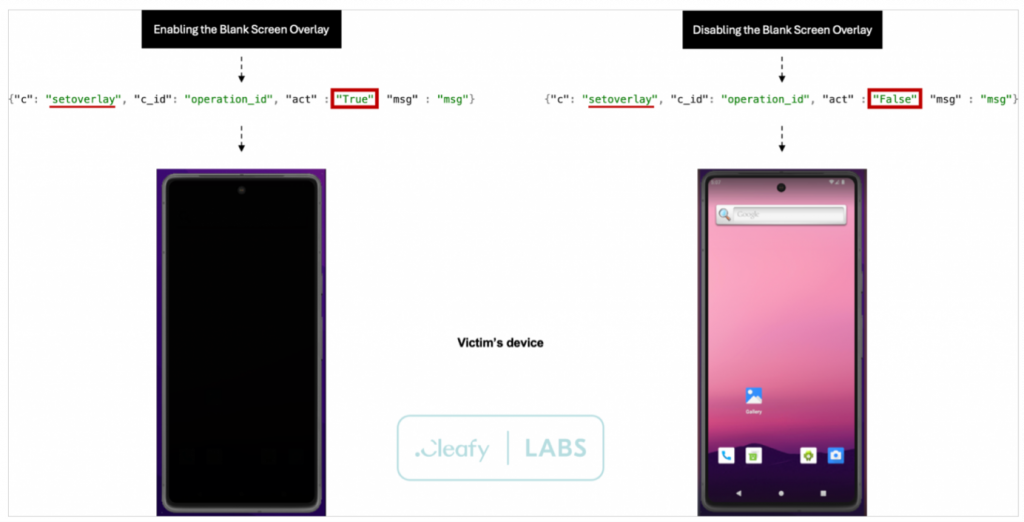
The “setoverlay” command is interesting because it enables remote attackers to take misleadingoperations such as making the device appear locked/shut down to conceal malicious ODF activity running in the background.
Black screen overlay in action
Source: Cleafy
The ability to capture screenshots is also a significant improvement, allowing threat actors a new opportunity to steal critical data from infected devices.
Overall, the Medusa mobile banking trojan campaign looks to be expanding its target base and getting more elusive to create the proper infrastructure for larger-scale deployment and a greater number of potential victims. Although Cleafy hasn’t spotted any dropper apps hosted on Google Play, with more and more hackers joining the MaaS, it is foreseeable that distribution techniques will widen and become increasingly sophisticated.
How to overcome and eradicate the Medusa Malware variants for Android Users?
Quixxi scans the device environment for malware like Medusa and restricts app launch and function if it finds the device infected with malware signatures. Quixxi reports this incident on the dashboard with traceable info for further investigation.
To learn more about how Quixxi can protect you from Medusa Malware, click the button below to talk to an expert.
By leveraging these capabilities, developers and organisations can implement a proactive strategy against Medusa malware and other sophisticated threats:
- Prevention: Through comprehensive vulnerability assessments (SAST, DAST), developers can identify and remediate security flaws before deploying their apps. This reduces the likelihood of apps becoming susceptible to Medusa through known entry points.
- Protection: Quixxi’s shielding technology ensures that even if a device is compromised, the app’s critical components remain secure, preventing unauthorised access to sensitive data or functionalities.
- Detection and Response: Continuous monitoring and threat analytics enable swift detection of Medusa’s activities, allowing for immediate response actions such as quarantining affected devices or triggering alerts for users and administrators.
Ultimately, by integrating Quixxi’s App Shield and leveraging its suite of security offerings, developers can enhance the security posture of their Android applications significantly. This proactive approach not only protects users from Medusa and similar malware but also fosters a safer mobile ecosystem overall.






