iOS App Shield
Introduction
Quixxi Security is usable by enterprises and mobile app developers to secure their mobile apps from piracy, revenue loss, IP theft, loss of user data , hacking and cracking. Quixxi Security ensures your application is fully protected with our multi-layered encryption engine that prevents your application from being reverse engineered and tampered with
Steps to apply Quixxi Security to iOS app
Please follow the steps below to protect your iOS application with Quixxi Security
- Create a new app in Quixxi Portal using the “Add New” box
- In the “Create your app” dialog give a name to your application and click “Continue”
- Click the newly created app and choose “Shield” tab in the header bar
- Drag and Drop your IPA file and click on “Next”
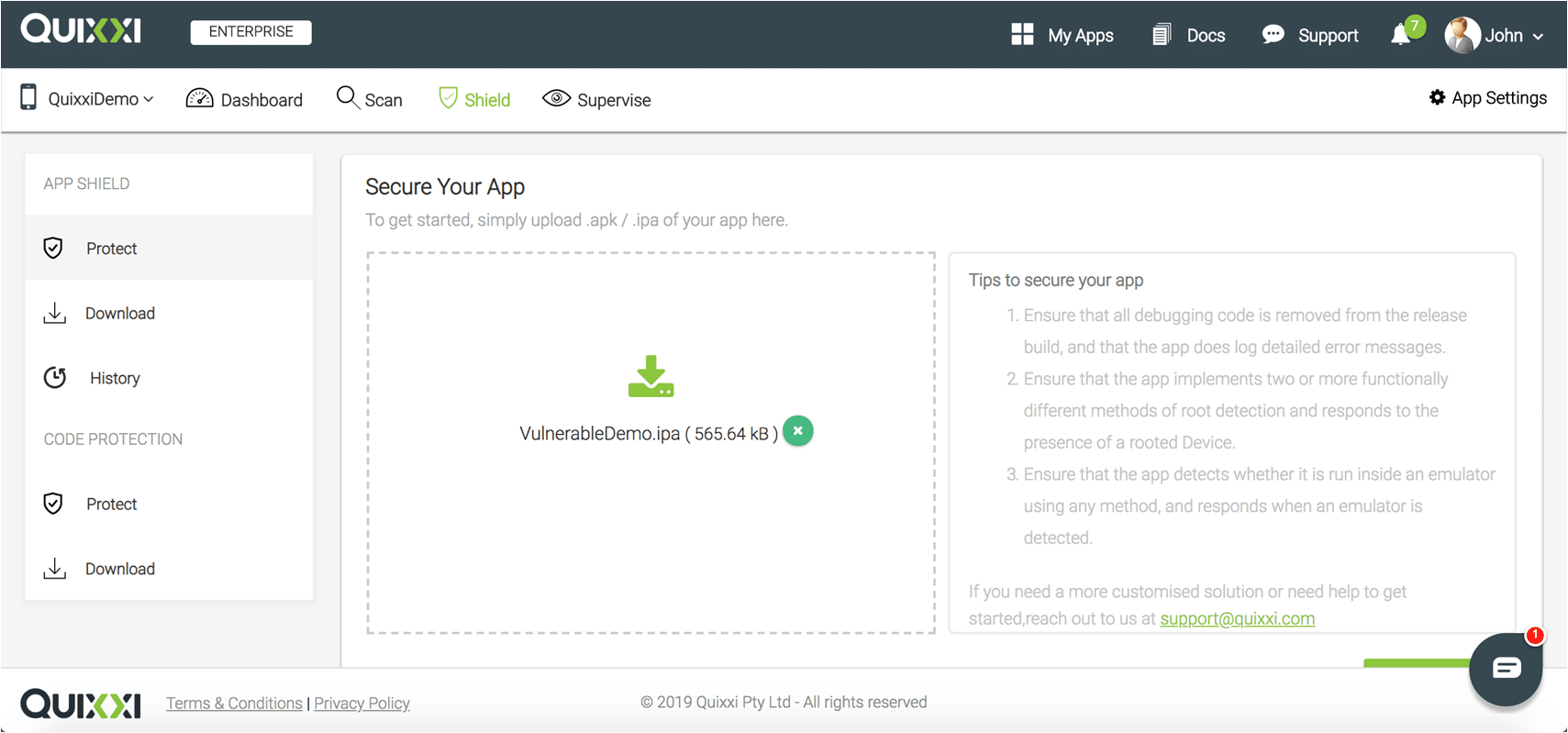
- Now start configuring the security options according to your needs. You can find their detailed explanations here. Once done please click on “Next” to start protecting your app
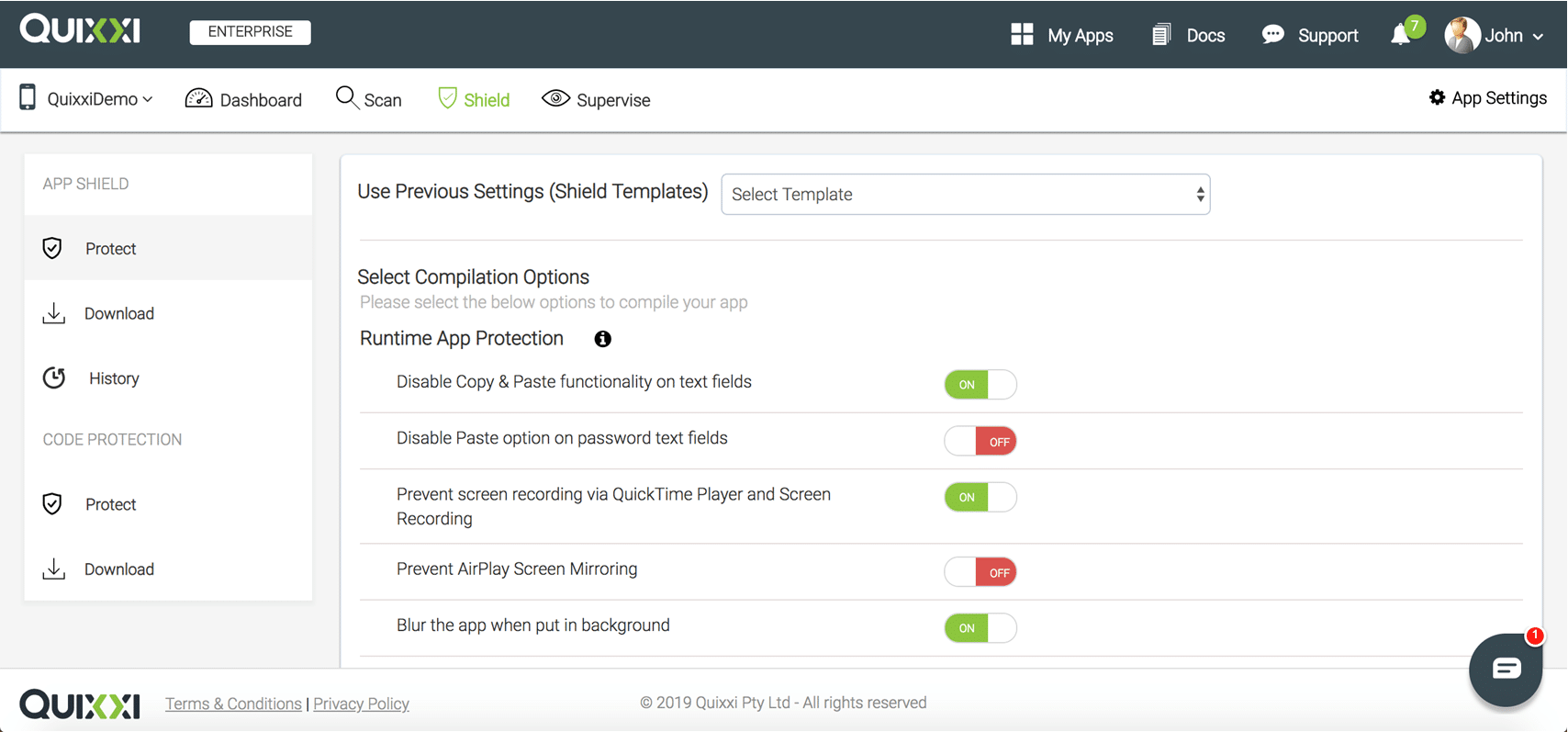
- Once the compilation is over you will be redirected to the “Download” section. Your protected app will be available clicking on “Download Protected App”
- If you decided to sign the ipa locally instead of uploading the Development/Distribution certificate in Quixxi Portal while applying the Shield you MUST now sign the downloaded ipa file to have it working on mobile. You can find the detailed manual signing procedure here
iOS Shield options description
Quixxi Shield is available only for plans that are equal or superior to the Pro one
IMPORTANT – in all the options involving the app termination please bear in mind that the final user will NOT be notified about the specific cause for security reasons, so use the options wisely
Runtime App Protection
Disable copy & paste functionality on standard text fields
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will search the UITextField elements in the app. When found, Quixxi Shield will insert the logic to prevent copying and pasting the content outside the app
IMPORTANT – the copy and paste protection applies ONLY when the copied content is taken from UITextField elements
Disable paste option on password text fields
This option is set to OFF state by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi Shield will search the UITextField elements which are set as secureTextEntry. When found, Quixxi Shield will insert the logic to prevent pasting the content into the password text fields
Prevent screen recording via QuickTime Player and Screen Recording
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to prevent the app to be recorded using QuickTime Player on Mac [Movie Recording functionality] or via Screen Recording on iPhone for iOS 11 and later versions. If the user tries to record the mobile screen in such conditions then Quixxi Shield will prompt a white screen with the message “Can’t record the mobile screen”
Prevent AirPlay Screen Mirroring
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to prevent the AirPlay screen mirroring. If the user tries to share the mobile screen in such conditions then Quixxi Shield will prompt a white screen for the mirrored one with the message “Can’t perform screen mirroring”
Blur the app when put in background
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to blur the app preview when the app is put in background
Terminate the app running in jailbroken devices
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to terminate the app when executed in a jailbroken phone. This option can be used to stop the app regardless of the store from where it was downloaded and installed
Allow apps installed from AppStore to bypass the jailbreak protection
This option is set to OFF State by default and can be modified only when the previous “Terminate the app running in jailbroken devices” is ON. If this option is ON, Quixxi Shield will insert the logic to terminate the app exclusively on those devices which did NOT install the app from App Store
IMPORTANT – This option must be chosen VERY carefully. We introduced it to let all the customers who downloaded from safe markets use the app on jailbroken devices. This is extremely important for paid apps, because customers who are denied the access after a regular purchase can destroy its reputation on the markets. On the other side please consider that the possibility itself to run the app on jailbroken devices – even though only under controlled conditions – will make you fail advanced security assessments, especially if the data handled by the app are sensitive [as in fintech, healthcare, etc.]
Tamper Protection
Report to Quixxi portal after threat detection
This option is set to ON by default and can be modified. If this option is ON, Quixxi Shield will report on Quixxi portal and in real-time the occurrence of the following threats, when the related shield option is selected: app not passing the integrity check, app attached to debugger, app running in a jailbroken device and published or TestFlight app later resigned
Validate app integrity
This option is set to ON by default and can’t be modified. If this option is ON, Quixxi Shield will insert the logic to verify the integrity of the app at runtime. If the check fails, then the app will be immediately terminated
Terminate your Published or TestFlight app when resigned
This option is set to OFF by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to verify that the original application has not been resigned after being downloaded from the App Store or TestFlight. If the check fails, then the app will be immediately terminated
IMPORTANT – This option is NOT intended to be applied on debug builds. In this case the app will be immediately terminated because the debug versions lack of the encryption, which is instead expected to be found on Published or TestFlight apps
Terminate the app when running with the debugger attached
This option is set to OFF by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to immediately terminate the app whenever a debugger is attached
Encrypt the UserDefaults values
This option is set to OFF by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi Shield will insert the logic to encrypt the values before storing them in UserDefaults
IMPORTANT – Once this option is switched ON for a particular app version then the same setting must be applied also for the future releases or you will likely experience app crashes. The technical reason is that if e.g. version 3.2 of your app makes use of the automated encryption/decryption logic for the UserDefaults then version 3.3 and following will need the same automated mechanism when dealing with previously encrypted content
Encrypt files created and used by the application at runtime
This option is set to OFF by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi Shield will insert the logic to encrypt the content of runtime files before storing it in the app sandbox
IMPORTANT – Once this option is switched ON for a particular app version then the same setting must be applied also for the future releases or you will likely experience app crashes. The technical reason is that if e.g. version 3.2 of your app makes use of the automated encryption/decryption logic for the files produced at runtime then version 3.3 and following will need the same automated mechanism when dealing with previously encrypted content
Secure Communication
SSL certificate validation via SSL pinning
This option is set to OFF state by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi will hardcode the public key used by the mobile app [i.e. the client] to authenticate the server. In this way the app can ignore the device trust store and rely only on the assigned one[s]. The developer will enter the URLs making use of the public key to be verified. Quixxi will retrieve their public keys and include them within the logic needed to increase the security level of the app data in transit
App Signing
Sign your IPA after applying security shield
This option is set to OFF by default and can be modified. If this option is ON, Quixxi Shield will first apply its security layer and then sign this secured IPA with your Certificate and Provision Profile. So the protected app that you will receive from the Download section of our portal is ready to be directly published on the App Store or directly installed in your provisioned devices. Of course you can also choose to benefit from Quixxi Shield effects without revealing us your certificates, signing the IPA on your own machine later
IMPORTANT – from a pure functional point of view signing the IPA on Quixxi portal or locally makes no difference at all. But forgetting to sign it dramatically does. Device does not allow to install any unsigned IPA and any attempt to bypass this rule will fail. Moreover the App Store will not allow to publish an unsigned IPA
NOTE: if you need a protected and signed test app you will first need to access the “Edit iOS Provisioning Profile (Development)” window in the Apple portal, giving the permission to your testers. Then you will just need to provide the Development Certificate & Development Provision in the Quixxi boxes
Supervise configuration
Send events and device info to Quixxi portal [basic version]
This option is set to ON by default and can’t be modified. If this option is ON, Quixxi Shield will insert the logics to log basic events [new user and app start] plus other basic data like store used for the download, device vendor, model, operative system, app version, etc. In this case Quixxi will receive the data and automatically organize their display on the portal in pie charts and lists
Send crash reports to Quixxi portal
This option is set to OFF by default and can be modified. If this option is ON, Quixxi shield will insert the logics to detect the app crashes, filing each of them on Quixxi portal together with the debugging files needed to bugfix the issues. Moreover we will directly embed on our website a research on StackOverflow for each of the problems that were collected
Steps to manually sign an IPA
- Select “Shield” tab in the header bar, click on “Download” in the left menu, choose the Apple icon in the top right corner and click on “Download the protected app”
- Unzip the IPA
- Sign the Plugins
- Sign the Watch Kit Extensions
– Sign the watch kit plugins– Sign the watch kit app
- Sign the QuixxiShield
- Sign the application
– Using same provisioning profile [Recommended]NOTE: you can get your Signing Identity name in KeyChain Access. Please refer to the screenshot below
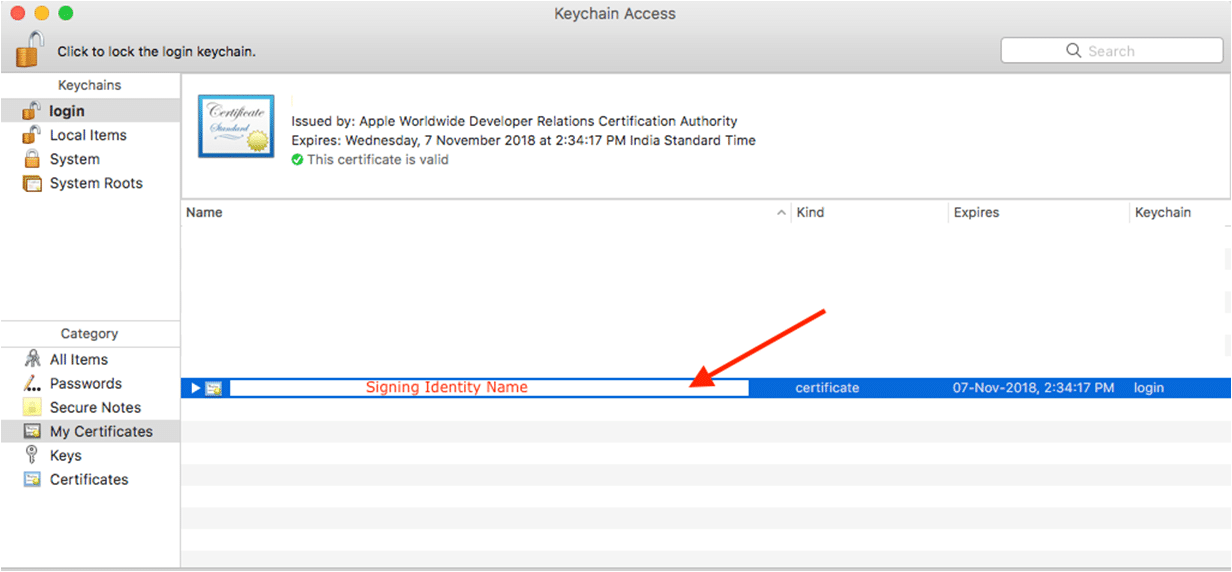
– Using different provisioning profile
- Copy the provisioning profile into the application package
- Reveal the provisioning profile content
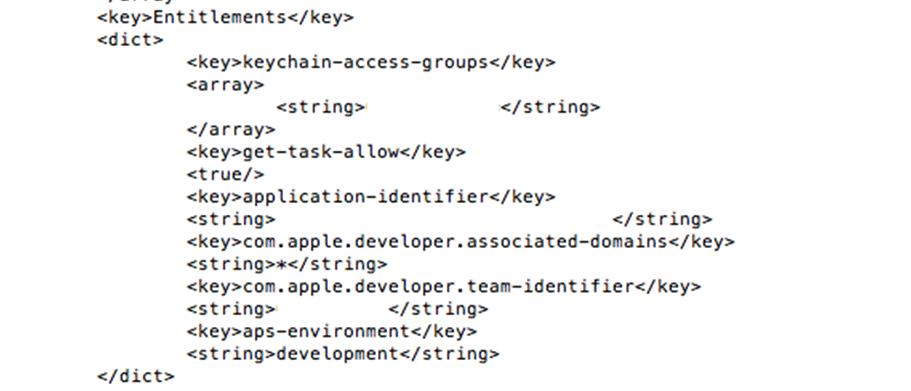
- Locate the entitlements section and copy the Entitlements dictionary
- Create ENTITLEMENT.plist file and paste the content copied in step 2. Now your file looks like below
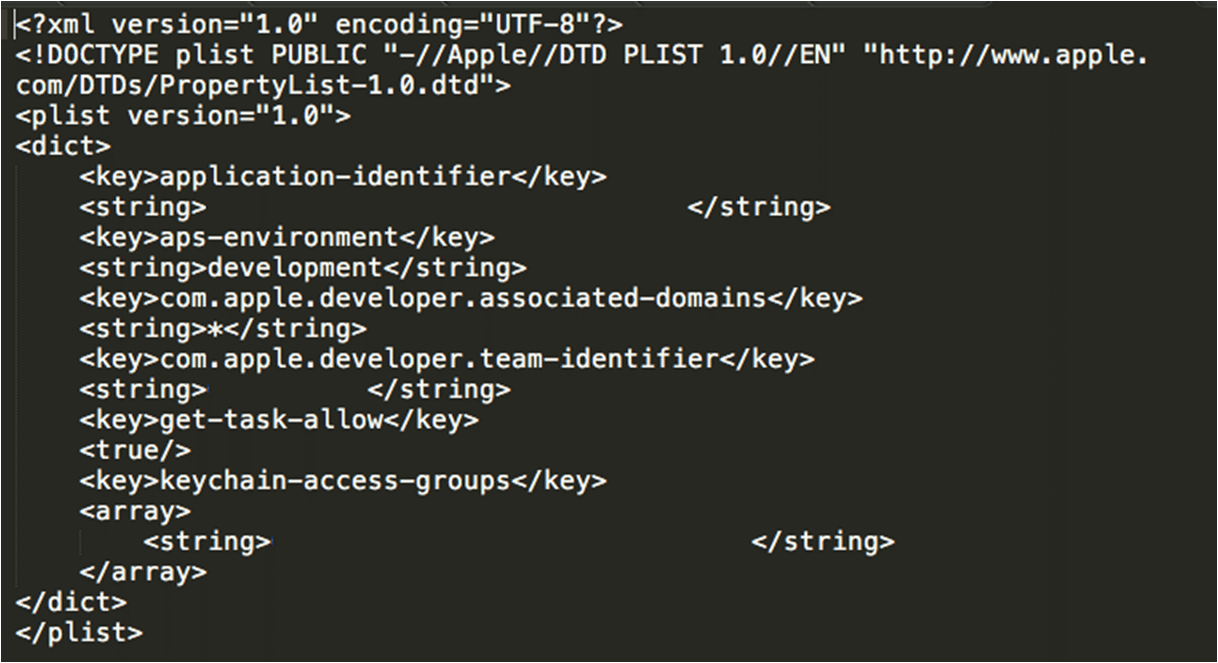
- Finally sign the IPA file
- Copy the provisioning profile into the application package
- Repack the IPA
– method 1Note: UNPACKED_FOLDER may contain the payload and other swift support files
– method 2
Select the Payload and Swift support files and compress then change the file extension from .zip to .ipa
iOS App Shield
Introduction
Quixxi Security is usable by enterprises and mobile app developers to secure their mobile apps from piracy, revenue loss, IP theft, loss of user data , hacking and cracking. Quixxi Security ensures your application is fully protected with our multi-layered encryption engine that prevents your application from being reverse engineered and tampered with
Steps to apply Quixxi Security to iOS app
Please follow the steps below to protect your iOS application with Quixxi Security
- Create a new app in Quixxi Portal using the “Add New” box
- In the “Create your app” dialog give a name to your application and click “Continue”
- Click the newly created app and choose “Shield” tab in the header bar
- Drag and Drop your IPA file and click on “Next”

- Now start configuring the security options according to your needs. You can find their detailed explanations here. Once done please click on “Next” to start protecting your app

- Once the compilation is over you will be redirected to the “Download” section. Your protected app will be available clicking on “Download Protected App”
- If you decided to sign the ipa locally instead of uploading the Development/Distribution certificate in Quixxi Portal while applying the Shield you MUST now sign the downloaded ipa file to have it working on mobile. You can find the detailed manual signing procedure here
iOS Shield options description
Quixxi Shield is available only for plans that are equal or superior to the Pro one
IMPORTANT – in all the options involving the app termination please bear in mind that the final user will NOT be notified about the specific cause for security reasons, so use the options wisely
Runtime App Protection
Disable copy & paste functionality on standard text fields
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will search the UITextField elements in the app. When found, Quixxi Shield will insert the logic to prevent copying and pasting the content outside the app
IMPORTANT – the copy and paste protection applies ONLY when the copied content is taken from UITextField elements
Disable paste option on password text fields
This option is set to OFF state by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi Shield will search the UITextField elements which are set as secureTextEntry. When found, Quixxi Shield will insert the logic to prevent pasting the content into the password text fields
Prevent screen recording via QuickTime Player and Screen Recording
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to prevent the app to be recorded using QuickTime Player on Mac [Movie Recording functionality] or via Screen Recording on iPhone for iOS 11 and later versions. If the user tries to record the mobile screen in such conditions then Quixxi Shield will prompt a white screen with the message “Can’t record the mobile screen”
Prevent AirPlay Screen Mirroring
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to prevent the AirPlay screen mirroring. If the user tries to share the mobile screen in such conditions then Quixxi Shield will prompt a white screen for the mirrored one with the message “Can’t perform screen mirroring”
Blur the app when put in background
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to blur the app preview when the app is put in background
Terminate the app running in jailbroken devices
This option is set to OFF state by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to terminate the app when executed in a jailbroken phone. This option can be used to stop the app regardless of the store from where it was downloaded and installed
Allow apps installed from AppStore to bypass the jailbreak protection
This option is set to OFF State by default and can be modified only when the previous “Terminate the app running in jailbroken devices” is ON. If this option is ON, Quixxi Shield will insert the logic to terminate the app exclusively on those devices which did NOT install the app from App Store
IMPORTANT – This option must be chosen VERY carefully. We introduced it to let all the customers who downloaded from safe markets use the app on jailbroken devices. This is extremely important for paid apps, because customers who are denied the access after a regular purchase can destroy its reputation on the markets. On the other side please consider that the possibility itself to run the app on jailbroken devices – even though only under controlled conditions – will make you fail advanced security assessments, especially if the data handled by the app are sensitive [as in fintech, healthcare, etc.]
Tamper Protection
Report to Quixxi portal after threat detection
This option is set to ON by default and can be modified. If this option is ON, Quixxi Shield will report on Quixxi portal and in real-time the occurrence of the following threats, when the related shield option is selected: app not passing the integrity check, app attached to debugger, app running in a jailbroken device and published or TestFlight app later resigned
Validate app integrity
This option is set to ON by default and can’t be modified. If this option is ON, Quixxi Shield will insert the logic to verify the integrity of the app at runtime. If the check fails, then the app will be immediately terminated
Terminate your Published or TestFlight app when resigned
This option is set to OFF by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to verify that the original application has not been resigned after being downloaded from the App Store or TestFlight. If the check fails, then the app will be immediately terminated
IMPORTANT – This option is NOT intended to be applied on debug builds. In this case the app will be immediately terminated because the debug versions lack of the encryption, which is instead expected to be found on Published or TestFlight apps
Terminate the app when running with the debugger attached
This option is set to OFF by default and can be modified. If this option is ON, Quixxi Shield will insert the logic to immediately terminate the app whenever a debugger is attached
Encrypt the UserDefaults values
This option is set to OFF by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi Shield will insert the logic to encrypt the values before storing them in UserDefaults
IMPORTANT – Once this option is switched ON for a particular app version then the same setting must be applied also for the future releases or you will likely experience app crashes. The technical reason is that if e.g. version 3.2 of your app makes use of the automated encryption/decryption logic for the UserDefaults then version 3.3 and following will need the same automated mechanism when dealing with previously encrypted content
Encrypt files created and used by the application at runtime
This option is set to OFF by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi Shield will insert the logic to encrypt the content of runtime files before storing it in the app sandbox
IMPORTANT – Once this option is switched ON for a particular app version then the same setting must be applied also for the future releases or you will likely experience app crashes. The technical reason is that if e.g. version 3.2 of your app makes use of the automated encryption/decryption logic for the files produced at runtime then version 3.3 and following will need the same automated mechanism when dealing with previously encrypted content
Secure Communication
SSL certificate validation via SSL pinning
This option is set to OFF state by default and can be modified. This option applies ONLY to native apps. If this option is ON, Quixxi will hardcode the public key used by the mobile app [i.e. the client] to authenticate the server. In this way the app can ignore the device trust store and rely only on the assigned one[s]. The developer will enter the URLs making use of the public key to be verified. Quixxi will retrieve their public keys and include them within the logic needed to increase the security level of the app data in transit
App Signing
Sign your IPA after applying security shield
This option is set to OFF by default and can be modified. If this option is ON, Quixxi Shield will first apply its security layer and then sign this secured IPA with your Certificate and Provision Profile. So the protected app that you will receive from the Download section of our portal is ready to be directly published on the App Store or directly installed in your provisioned devices. Of course you can also choose to benefit from Quixxi Shield effects without revealing us your certificates, signing the IPA on your own machine later
IMPORTANT – from a pure functional point of view signing the IPA on Quixxi portal or locally makes no difference at all. But forgetting to sign it dramatically does. Device does not allow to install any unsigned IPA and any attempt to bypass this rule will fail. Moreover the App Store will not allow to publish an unsigned IPA
NOTE: if you need a protected and signed test app you will first need to access the “Edit iOS Provisioning Profile (Development)” window in the Apple portal, giving the permission to your testers. Then you will just need to provide the Development Certificate & Development Provision in the Quixxi boxes
Supervise configuration
Send events and device info to Quixxi portal [basic version]
This option is set to ON by default and can’t be modified. If this option is ON, Quixxi Shield will insert the logics to log basic events [new user and app start] plus other basic data like store used for the download, device vendor, model, operative system, app version, etc. In this case Quixxi will receive the data and automatically organize their display on the portal in pie charts and lists
Send crash reports to Quixxi portal
This option is set to OFF by default and can be modified. If this option is ON, Quixxi shield will insert the logics to detect the app crashes, filing each of them on Quixxi portal together with the debugging files needed to bugfix the issues. Moreover we will directly embed on our website a research on StackOverflow for each of the problems that were collected
Steps to manually sign an IPA
- Select “Shield” tab in the header bar, click on “Download” in the left menu, choose the Apple icon in the top right corner and click on “Download the protected app”
- Unzip the IPA
- Sign the Plugins
- Sign the Watch Kit Extensions
– Sign the watch kit plugins– Sign the watch kit app
- Sign the QuixxiShield
- Sign the application
– Using same provisioning profile [Recommended]NOTE: you can get your Signing Identity name in KeyChain Access. Please refer to the screenshot below

– Using different provisioning profile
- Copy the provisioning profile into the application package
- Reveal the provisioning profile content

- Locate the entitlements section and copy the Entitlements dictionary
- Create ENTITLEMENT.plist file and paste the content copied in step 2. Now your file looks like below

- Finally sign the IPA file
- Copy the provisioning profile into the application package
- Repack the IPA
– method 1Note: UNPACKED_FOLDER may contain the payload and other swift support files
– method 2
Select the Payload and Swift support files and compress then change the file extension from .zip to .ipa